Hello @francescouk, thanks for your question!
Yes, it's possible to create rule exceptions using IP address ranges, like the example you provided above.
Detailed below is a breakdown of how I verified this by:
- Enabling the rule
- Indexing some test data (before creating the exception)
- Creating an exception
- Indexing more test data, to verify that the exception is working
Enabling the rule
The screenshot below illustrates enabling the SMB (Windows File Sharing) Activity to the Internet rule in your example:
Indexing some test data (before creating the exception)
Before we add an exception, we want to verify the SMB (Windows File Sharing) Activity to the Internet rule is creating alerts.
To simplify this testing, we'll index some sample documents that:
- Match the criteria of the
SMB (Windows File Sharing) Activity to the Internet rule
- Also have
source.ip and destination.ip addresses that match the example
- Have a
host.name field with some values that will help us test the rule and the exception
Since the auditbeat index is included in the SMB (Windows File Sharing) Activity to the Internet rule, we can run:
auditbeat setup
on the command line, which creates an empty auditbeat index we can use for testing.
Next, in the Kibana Dev Tools Console, execute the following query to index a test document:
POST auditbeat-8.1.1/_doc/
{
"@timestamp": "2022-07-21T20:29:17.054Z",
"event": {
"category": "network"
},
"host": {
"name": "before-exception-1"
},
"network": {
"transport": "tcp"
},
"destination": {
"ip": "200.1.0.0",
"port": 139
},
"source": {
"ip": "192.168.0.1"
},
"foo": "test"
}
Note the host.name in the example above is before-exception-1.
After executing the query above, edit it such that the new value of host.name is:
before-exception-2
and then run the updated query to index a second document.
Through the steps above, we indexed two documents, (based on the example), that match the criteria of the SMB (Windows File Sharing) Activity to the Internet rule.
In the next section, we will see alerts generated for the two documents we indexed.
Creating an exception
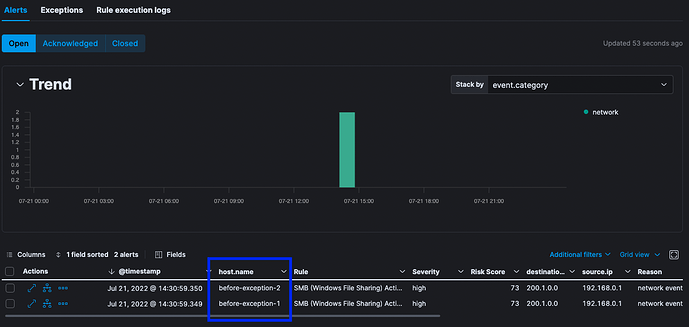
After several minutes, Alerts were opened for each of the two test documents, per the screenshot below from the SMB (Windows File Sharing) Activity to the Internet rule details page:
Note the before-exception-1, and before-exception-2 values for the host.name column in the screenshot above.
To begin creating an exception, click the Add rule exception action menu item, shown in the screenshot below:
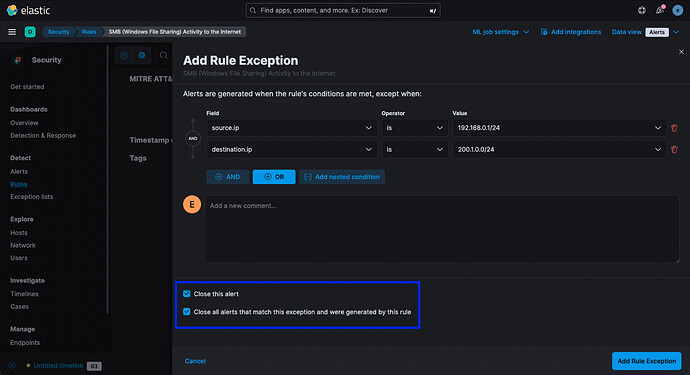
Next, we'll enter the criteria:
source.ip is 192.168.0.1/24 AND destination.ip is 200.1.0.0/24
in the Add Rule Exception flyout, shown in the screenshot below:
We can verify the new exception would have matched the alerts that were already opened by checking the both of the following options in the screenshot below:
Close this alertClose all alerts that match this exception and were generated by this rule
Click Add Rule Exception.
After clicking Add Rule Exception, all the Open SMB (Windows File Sharing) Activity to the Internet alerts are now Closed, proving our exception would have matched them, per the screenshot below:
Indexing more test data, to verify that the exception is working
To prove the exception is working, let's index two more documents:
- One document that will match the exception
- One document that will NOT match the exception
First, let's index the following document, which Is identical to the last document, except:
- It has an updated
@timestamp
- It has a
host.name with the value this-will-match-the-exception:
POST auditbeat-8.1.1/_doc/
{
"@timestamp": "2022-07-21T21:35:09.235Z",
"event": {
"category": "network"
},
"host": {
"name": "this-will-match-the-exception"
},
"network": {
"transport": "tcp"
},
"destination": {
"ip": "200.1.0.0",
"port": 139
},
"source": {
"ip": "192.168.0.1"
},
"foo": "test"
}
Next, let's index one more document, which is identical to the previous document, except:
- It has a
destination.ip that will NOT match the exception
- It has a
host.name with the value this-will-NOT-match-the-exception
POST auditbeat-8.1.1/_doc/
{
"@timestamp": "2022-07-21T21:35:09.235Z",
"event": {
"category": "network"
},
"host": {
"name": "this-will-NOT-match-the-exception"
},
"network": {
"transport": "tcp"
},
"destination": {
"ip": "123.4.5.6",
"port": 139
},
"source": {
"ip": "192.168.0.1"
},
"foo": "test"
}
After several minutes, we can see via the SMB (Windows File Sharing) Activity to the Internet rules details page that we have one new Open alert:
- The document with the
host.name: this-will-match-the-exception was indexed, but an alert was not generated for it
- One alert was generated, for the
host.name: this-will-NOT-match-the-exception.
Conclusion
The details in the previous sections demonstrate it's possible to create a rule exception based on IP address ranges.