Hello,
I have been using ELK for a while and I am trying to retrieve the logs from a Wifi controller (Aruba Mobility Master). I checked with Wireshark, and I'm getting my syslog packets fine. However, logstash makes an error for each received packet:
C:\data\logstash>bin\logstash -f config\logstash-test-aruba.conf
"Using bundled JDK: ""
OpenJDK 64-Bit Server VM warning: Option UseConcMarkSweepGC was deprecated in version 9.0 and will likely be removed in a future release.
C:/data/logstash/vendor/bundle/jruby/2.5.0/gems/bundler-1.17.3/lib/bundler/rubygems_integration.rb:200: warning: constant Gem::ConfigMap is deprecated
Sending Logstash logs to C:/data/logstash/logs which is now configured via log4j2.properties
[2021-08-13T10:59:24,178][INFO ][logstash.runner ] Log4j configuration path used is: C:\data\logstash\config\log4j2.properties
[2021-08-13T10:59:24,188][INFO ][logstash.runner ] Starting Logstash {"logstash.version"=>"7.14.0", "jruby.version"=>"jruby 9.2.19.0 (2.5.8) 2021-06-15 55810c552b OpenJDK 64-Bit Server VM 11.0.11+9 on 11.0.11+9 +indy +jit [mswin32-x86_64]"}
[2021-08-13T10:59:24,278][WARN ][logstash.config.source.multilocal] Ignoring the 'pipelines.yml' file because modules or command line options are specified
[2021-08-13T10:59:25,785][INFO ][logstash.agent ] Successfully started Logstash API endpoint {:port=>9600}
[2021-08-13T10:59:26,301][INFO ][org.reflections.Reflections] Reflections took 53 ms to scan 1 urls, producing 120 keys and 417 values
[2021-08-13T10:59:27,121][INFO ][logstash.outputs.elasticsearch][main] New Elasticsearch output {:class=>"LogStash::Outputs::ElasticSearch", :hosts=>["//127.0.0.1:9200"]}
[2021-08-13T10:59:27,402][INFO ][logstash.outputs.elasticsearch][main] Elasticsearch pool URLs updated {:changes=>{:removed=>[], :added=>[http://127.0.0.1:9200/]}}
[2021-08-13T10:59:27,534][WARN ][logstash.outputs.elasticsearch][main] Restored connection to ES instance {:url=>"http://127.0.0.1:9200/"}
[2021-08-13T10:59:27,572][INFO ][logstash.outputs.elasticsearch][main] Elasticsearch version determined (7.14.0) {:es_version=>7}
[2021-08-13T10:59:27,572][WARN ][logstash.outputs.elasticsearch][main] Detected a 6.x and above cluster: the `type` event field won't be used to determine the document _type {:es_version=>7}
[2021-08-13T10:59:27,619][WARN ][logstash.outputs.elasticsearch][main] Configuration is data stream compliant but due backwards compatibility Logstash 7.x will not assume writing to a data-stream, default behavior will change on Logstash 8.0 (set `data_stream => true/false` to disable this warning)
[2021-08-13T10:59:27,634][WARN ][logstash.outputs.elasticsearch][main] Configuration is data stream compliant but due backwards compatibility Logstash 7.x will not assume writing to a data-stream, default behavior will change on Logstash 8.0 (set `data_stream => true/false` to disable this warning)
[2021-08-13T10:59:27,688][INFO ][logstash.outputs.elasticsearch][main] Using a default mapping template {:es_version=>7, :ecs_compatibility=>:disabled}
[2021-08-13T10:59:27,719][INFO ][logstash.javapipeline ][main] Starting pipeline {:pipeline_id=>"main", "pipeline.workers"=>4, "pipeline.batch.size"=>125, "pipeline.batch.delay"=>50, "pipeline.max_inflight"=>500, "pipeline.sources"=>["C:/data/logstash/config/logstash-test-aruba.conf"], :thread=>"#<Thread:0x15ffbb2f run>"}
[2021-08-13T10:59:28,405][INFO ][logstash.javapipeline ][main] Pipeline Java execution initialization time {"seconds"=>0.69}
[2021-08-13T10:59:28,437][INFO ][logstash.javapipeline ][main] Pipeline started {"pipeline.id"=>"main"}
[2021-08-13T10:59:28,474][INFO ][logstash.inputs.udp ][main][171962edfa0cfd61c4a7d15d6f352f1f97843ffcb9f46c020c0a4481b88672af] Starting UDP listener {:address=>"0.0.0.0:514"}
[2021-08-13T10:59:28,506][INFO ][logstash.agent ] Pipelines running {:count=>1, :running_pipelines=>[:main], :non_running_pipelines=>[]}
[2021-08-13T10:59:28,521][INFO ][logstash.inputs.udp ][main][171962edfa0cfd61c4a7d15d6f352f1f97843ffcb9f46c020c0a4481b88672af] UDP listener started {:address=>"0.0.0.0:514", :receive_buffer_bytes=>"65536", :queue_size=>"2000"}
[2021-08-13T10:59:37,183][ERROR][logstash.codecs.json ][main][171962edfa0cfd61c4a7d15d6f352f1f97843ffcb9f46c020c0a4481b88672af] JSON parse error, original data now in message field {:error=>#<LogStash::Json::ParserError: Unexpected character ('<' (code 60)): expected a valid value (number, String, array, object, 'true', 'false' or 'null')
at [Source: (String)"<139>Aug 13 10:59:37 2021 MC72-WI-AS1-06-A <MC72-WI-AS1-06-A 172.20.10.10> httpd[21903]: Could not retrieve the CSRF token from db inside mod_aruba_auth"; line: 1, column: 2]>, :data=>"<139>Aug 13 10:59:37 2021 MC72-WI-AS1-06-A <MC72-WI-AS1-06-A 172.20.10.10> httpd[21903]: Could not retrieve the CSRF token from db inside mod_aruba_auth"}
[2021-08-13T10:59:37,183][ERROR][logstash.codecs.json ][main][171962edfa0cfd61c4a7d15d6f352f1f97843ffcb9f46c020c0a4481b88672af] JSON parse error, original data now in message field {:error=>#<LogStash::Json::ParserError: Unexpected character ('<' (code 60)): expected a valid value (number, String, array, object, 'true', 'false' or 'null')
at [Source: (String)"<139>Aug 13 10:59:37 2021 MC72-WI-AS1-06-A <MC72-WI-AS1-06-A 172.20.10.10> httpd[21903]: Could not retrieve the CSRF token from db, called from arci_cgi"; line: 1, column: 2]>, :data=>"<139>Aug 13 10:59:37 2021 MC72-WI-AS1-06-A <MC72-WI-AS1-06-A 172.20.10.10> httpd[21903]: Could not retrieve the CSRF token from db, called from arci_cgi"}
[2021-08-13T10:59:37,198][ERROR][logstash.codecs.json ][main][171962edfa0cfd61c4a7d15d6f352f1f97843ffcb9f46c020c0a4481b88672af] JSON parse error, original data now in message field {:error=>#<LogStash::Json::ParserError: Unexpected character ('<' (code 60)): expected a valid value (number, String, array, object, 'true', 'false' or 'null')
at [Source: (String)"<139>Aug 13 10:59:37 2021 MC72-WI-AS1-06-A <MC72-WI-AS1-06-A 172.20.10.10> httpd[21903]: Could not retrieve the CSRF token from db inside mod_aruba_auth"; line: 1, column: 2]>, :data=>"<139>Aug 13 10:59:37 2021 MC72-WI-AS1-06-A <MC72-WI-AS1-06-A 172.20.10.10> httpd[21903]: Could not retrieve the CSRF token from db inside mod_aruba_auth"}
[2021-08-13T10:59:37,214][ERROR][logstash.codecs.json ][main][171962edfa0cfd61c4a7d15d6f352f1f97843ffcb9f46c020c0a4481b88672af] JSON parse error, original data now in message field {:error=>#<LogStash::Json::ParserError: Unexpected character ('<' (code 60)): expected a valid value (number, String, array, object, 'true', 'false' or 'null')
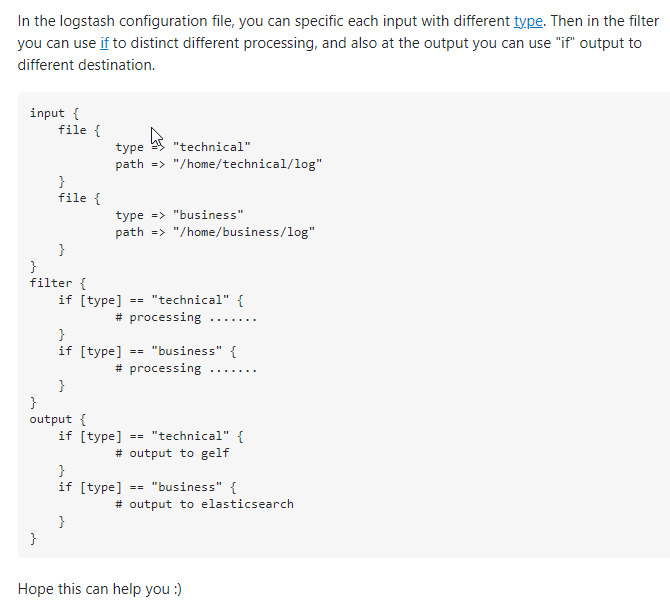
Below is the content of my logstash configuration file :
input {
udp {
host => "0.0.0.0"
port => 514
codec => "json"
type => "syslog"
}
}
# Every single log will be forwarded to ElasticSearch. If you are using another port, you should specify it here.
output {
if [type] == "syslog" {
elasticsearch {
hosts => [ "127.0.0.1:9200" ]
}
}
}
If any of you can help me so that I can receive and view these logs on Kibana... Thanks in advance for your help!
Best regards