Well, for now, I am just testing the configurations. If that is not too much disturbing, I will check later to start the service as "myself" and not as root. Because I will have to fix the rights to be able to do that, first. For now, I just discovering how the that works, and you help me a lot, for that. Therefore, ok, I take accounf of your suggestion. I will correct myself, in any cases.
What do you mean by "it is best to run Logstash as a system service, not using the command line" ? I thought the "-f' was to force the application to read again the configuration, to apply the changes, if changes there is.
Anyway, I tried your cmd, and I just obtain that :
root@Big-Monster:~# /usr/share/logstash/bin/logstash --path.settings /etc/logstash
OpenJDK 64-Bit Server VM warning: Option UseConcMarkSweepGC was deprecated in version 9.0 and will likely be removed in a future release.
WARNING: An illegal reflective access operation has occurred
WARNING: Illegal reflective access by com.headius.backport9.modules.Modules (file:/usr/share/logstash/logstash-core/lib/jars/jruby-complete-9.2.7.0.jar) to field java.io.FileDescriptor.fd
WARNING: Please consider reporting this to the maintainers of com.headius.backport9.modules.Modules
WARNING: Use --illegal-access=warn to enable warnings of further illegal reflective access operations
WARNING: All illegal access operations will be denied in a future release
Sending Logstash logs to /var/log/logstash which is now configured via log4j2.properties
[2023-11-21T16:18:53,056][INFO ][logstash.runner ] Starting Logstash {"logstash.version"=>"6.8.23"}
[2023-11-21T16:18:55,881][INFO ][logstash.pipeline ] Starting pipeline {:pipeline_id=>"cron", "pipeline.workers"=>4, "pipeline.batch.size"=>125, "pipeline.batch.delay"=>50}
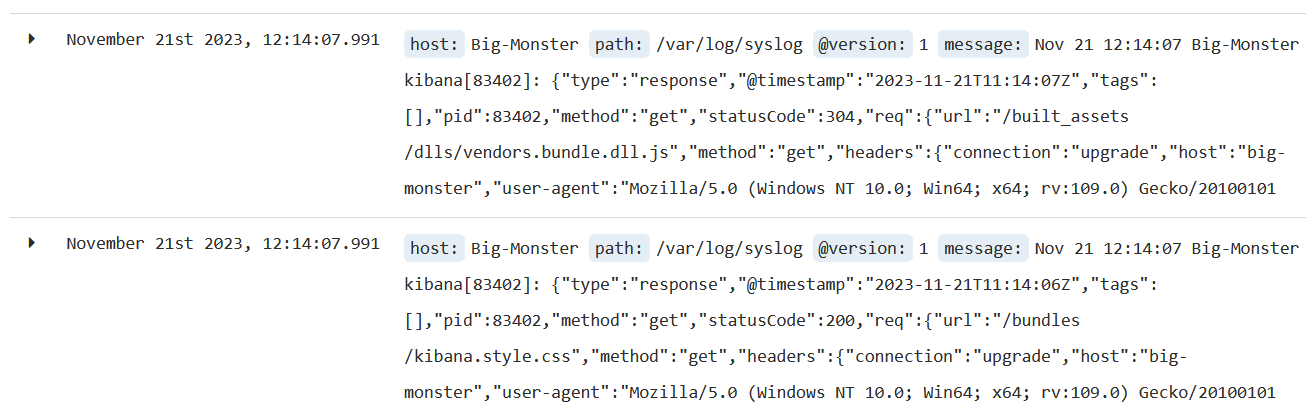
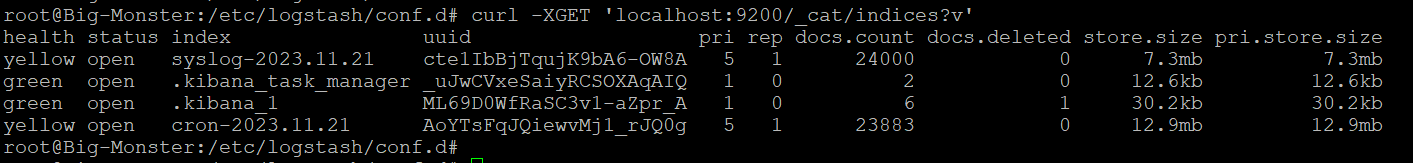
[2023-11-21T16:18:55,953][ERROR][logstash.agent ] Failed to execute action {:action=>LogStash::PipelineAction::Create/pipeline_id:syslog, :exception=>"LogStash::ConfigurationError", :message=>"Expected one of #, => at line 8, column 17 (byte 106) after input {\n file {\n id => \"TEST-Syslog\"\n path => [ \"/var/log/syslog\" ]\n }\n\noutput {\n elasticsearch ", :backtrace=>["/usr/share/logstash/logstash-core/lib/logstash/compiler.rb:41:in `compile_imperative'", "/usr/share/logstash/logstash-core/lib/logstash/compiler.rb:49:in `compile_graph'", "/usr/share/logstash/logstash-core/lib/logstash/compiler.rb:11:in `block in compile_sources'", "org/jruby/RubyArray.java:2577:in `map'", "/usr/share/logstash/logstash-core/lib/logstash/compiler.rb:10:in `compile_sources'", "org/logstash/execution/AbstractPipelineExt.java:151:in `initialize'", "/usr/share/logstash/logstash-core/lib/logstash/pipeline.rb:22:in `initialize'", "/usr/share/logstash/logstash-core/lib/logstash/pipeline.rb:90:in `initialize'", "/usr/share/logstash/logstash-core/lib/logstash/pipeline_action/create.rb:43:in `block in execute'", "/usr/share/logstash/logstash-core/lib/logstash/agent.rb:96:in `block in exclusive'", "org/jruby/ext/thread/Mutex.java:165:in `synchronize'", "/usr/share/logstash/logstash-core/lib/logstash/agent.rb:96:in `exclusive'", "/usr/share/logstash/logstash-core/lib/logstash/pipeline_action/create.rb:39:in `execute'", "/usr/share/logstash/logstash-core/lib/logstash/agent.rb:334:in `block in converge_state'"]}
[2023-11-21T16:18:56,259][INFO ][logstash.outputs.elasticsearch] Elasticsearch pool URLs updated {:changes=>{:removed=>[], :added=>[http://127.0.0.1:9200/]}}
[2023-11-21T16:18:56,446][WARN ][logstash.outputs.elasticsearch] Restored connection to ES instance {:url=>"http://127.0.0.1:9200/"}
[2023-11-21T16:18:56,492][INFO ][logstash.outputs.elasticsearch] ES Output version determined {:es_version=>6}
[2023-11-21T16:18:56,495][WARN ][logstash.outputs.elasticsearch] Detected a 6.x and above cluster: the `type` event field won't be used to determine the document _type {:es_version=>6}
[2023-11-21T16:18:56,514][INFO ][logstash.outputs.elasticsearch] New Elasticsearch output {:class=>"LogStash::Outputs::ElasticSearch", :hosts=>["//127.0.0.1"]}
[2023-11-21T16:18:56,527][INFO ][logstash.outputs.elasticsearch] Using default mapping template
[2023-11-21T16:18:56,554][INFO ][logstash.outputs.elasticsearch] Attempting to install template {:manage_template=>{"template"=>"logstash-*", "version"=>60001, "settings"=>{"index.refresh_interval"=>"5s"}, "mappings"=>{"_default_"=>{"dynamic_templates"=>[{"message_field"=>{"path_match"=>"message", "match_mapping_type"=>"string", "mapping"=>{"type"=>"text", "norms"=>false}}}, {"string_fields"=>{"match"=>"*", "match_mapping_type"=>"string", "mapping"=>{"type"=>"text", "norms"=>false, "fields"=>{"keyword"=>{"type"=>"keyword", "ignore_above"=>256}}}}}], "properties"=>{"@timestamp"=>{"type"=>"date"}, "@version"=>{"type"=>"keyword"}, "geoip"=>{"dynamic"=>true, "properties"=>{"ip"=>{"type"=>"ip"}, "location"=>{"type"=>"geo_point"}, "latitude"=>{"type"=>"half_float"}, "longitude"=>{"type"=>"half_float"}}}}}}}}
[2023-11-21T16:18:56,763][INFO ][logstash.inputs.file ] No sincedb_path set, generating one based on the "path" setting {:sincedb_path=>"/var/lib/logstash/plugins/inputs/file/.sincedb_9b0a58bc044ee19bc5c8f85111fa6dce", :path=>["/var/log/cron.log"]}
[2023-11-21T16:18:56,833][INFO ][filewatch.observingtail ] START, creating Discoverer, Watch with file and sincedb collections
[2023-11-21T16:18:57,079][INFO ][logstash.agent ] Successfully started Logstash API endpoint {:port=>9600}
(and nothing else. The command do not give me back the prompt, except if I do a ctrl C).
Best regards,
Chris