Hi,
I have been trying to configure Logstash Filebeat module. However I received message "No data has been received from this module yet".
I have installed Logstash. The following log from console:
Sending Logstash logs to /u01/logstash/logstash-7.8.0/logs which is now configured via log4j2.properties
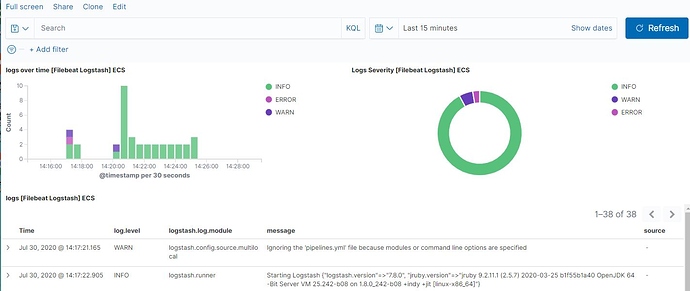
[2020-07-29T11:35:56,584][WARN ][logstash.config.source.multilocal] Ignoring the 'pipelines.yml' file because modules or command line options are specified
[2020-07-29T11:35:57,621][INFO ][logstash.runner ] Starting Logstash {"logstash.version"=>"7.8.0", "jruby.version"=>"jruby 9.2.11.1 (2.5.7) 2020-03-25 b1f55b1a40 OpenJDK 64-Bit Server VM 25.242-b08 on 1.8.0_242-b08 +indy +jit [linux-x86_64]"}
[2020-07-29T11:36:13,058][INFO ][org.reflections.Reflections] Reflections took 386 ms to scan 1 urls, producing 21 keys and 41 values
[2020-07-29T11:36:25,315][INFO ][logstash.outputs.elasticsearch][main] Elasticsearch pool URLs updated {:changes=>{:removed=>, :added=>[http://elastic:xxxxxx@ip:9200/]}}
[2020-07-29T11:36:27,234][WARN ][logstash.outputs.elasticsearch][main] Restored connection to ES instance {:url=>"http://elastic:xxxxxx@ip:9200/"}
[2020-07-29T11:36:27,730][INFO ][logstash.outputs.elasticsearch][main] ES Output version determined {:es_version=>7}
[2020-07-29T11:36:27,798][WARN ][logstash.outputs.elasticsearch][main] Detected a 6.x and above cluster: the type event field won't be used to determine the document _type {:es_version=>7}
[2020-07-29T11:36:28,303][INFO ][logstash.outputs.elasticsearch][main] New Elasticsearch output {:class=>"LogStash::Outputs::ElasticSearch", :hosts=>["//ip:9200"]}
[2020-07-29T11:36:28,627][INFO ][logstash.filters.geoip ][main] Using geoip database {:path=>"/u01/logstash/logstash-7.8.0/vendor/bundle/jruby/2.5.0/gems/logstash-filter-geoip-6.0.3-java/vendor/GeoLite2-City.mmdb"}
[2020-07-29T11:36:29,185][INFO ][logstash.outputs.elasticsearch][main] Using default mapping template
[2020-07-29T11:36:29,952][INFO ][logstash.outputs.elasticsearch][main] Attempting to install template {:manage_template=>{"index_patterns"=>"logstash-", "version"=>60001, "settings"=>{"index.refresh_interval"=>"5s", "number_of_shards"=>1, "index.lifecycle.name"=>"logstash-policy", "index.lifecycle.rollover_alias"=>"logstash"}, "mappings"=>{"dynamic_templates"=>[{"message_field"=>{"path_match"=>"message", "match_mapping_type"=>"string", "mapping"=>{"type"=>"text", "norms"=>false}}}, {"string_fields"=>{"match"=>"", "match_mapping_type"=>"string", "mapping"=>{"type"=>"text", "norms"=>false, "fields"=>{"keyword"=>{"type"=>"keyword", "ignore_above"=>256}}}}}], "properties"=>{"@timestamp"=>{"type"=>"date"}, "@version"=>{"type"=>"keyword"}, "geoip"=>{"dynamic"=>true, "properties"=>{"ip"=>{"type"=>"ip"}, "location"=>{"type"=>"geo_point"}, "latitude"=>{"type"=>"half_float"}, "longitude"=>{"type"=>"half_float"}}}}}}}
[2020-07-29T11:36:31,307][INFO ][logstash.javapipeline ][main] Starting pipeline {:pipeline_id=>"main", "pipeline.workers"=>1, "pipeline.batch.size"=>125, "pipeline.batch.delay"=>50, "pipeline.max_inflight"=>125, "pipeline.sources"=>["/u01/logstash/logstash-7.8.0/logconfig-v2.conf"], :thread=>"#<Thread:0x76af06d2 run>"}
[2020-07-29T11:36:39,353][INFO ][logstash.inputs.file ][main] No sincedb_path set, generating one based on the "path" setting {:sincedb_path=>"/u01/logstash/logstash-7.8.0/data/plugins/inputs/file/.sincedb_1c5ec98ac07a49055e612055de3d47da", :path=>["/u01/logstash/logstash-7.8.0/logs"]}
[2020-07-29T11:36:39,634][INFO ][logstash.inputs.beats ][main] Beats inputs: Starting input listener {:address=>"0.0.0.0:5044"}
[2020-07-29T11:36:39,985][INFO ][logstash.javapipeline ][main] Pipeline started {"pipeline.id"=>"main"}
[2020-07-29T11:36:41,030][INFO ][filewatch.observingtail ][main][39906785d3dba41157d0c9f4a80f330a3334999d5ceeae3d9a282f5b268b4227] START, creating Discoverer, Watch with file and sincedb collections
[2020-07-29T11:36:41,185][INFO ][logstash.agent ] Pipelines running {:count=>1, :running_pipelines=>[:main], :non_running_pipelines=>}
[2020-07-29T11:36:41,816][INFO ][org.logstash.beats.Server][main][c33a0efb6914b4a748d572e16a9c14e89c4ad6afef127dacfc7d7fa44ceaa8e2] Starting server on port: 5044
[2020-07-29T11:36:45,985][INFO ][logstash.agent ] Successfully started Logstash API endpoint {:port=>9600}
I have installed filebeat and the following log from console:
2020-07-29T11:54:24.608+0800 INFO instance/beat.go:647 Home path: [/u01/filebeat/filebeat-7.8.0-linux-x86_64] Config path: [/u01/filebeat/filebeat-7.8.0-linux-x86_64] Data path: [/u01/filebeat/filebeat-7.8.0-linux-x86_64/data] Logs path: [/u01/filebeat/filebeat-7.8.0-linux-x86_64/logs]
2020-07-29T11:54:24.608+0800 INFO instance/beat.go:655 Beat ID: 3884be0a-ca89-4fbd-ac71-94efd8420180
2020-07-29T11:54:27.611+0800 INFO [add_cloud_metadata] add_cloud_metadata/add_cloud_metadata.go:89 add_cloud_metadata: hosting provider type not detected.
2020-07-29T11:54:27.612+0800 INFO [seccomp] seccomp/seccomp.go:124 Syscall filter successfully installed
2020-07-29T11:54:27.612+0800 INFO [beat] instance/beat.go:983 Beat info {"system_info": {"beat": {"path": {"config": "/u01/filebeat/filebeat-7.8.0-linux-x86_64", "data": "/u01/filebeat/filebeat-7.8.0-linux-x86_64/data", "home": "/u01/filebeat/filebeat-7.8.0-linux-x86_64", "logs": "/u01/filebeat/filebeat-7.8.0-linux-x86_64/logs"}, "type": "filebeat", "uuid": "3884be0a-ca89-4fbd-ac71-94efd8420180"}}}
2020-07-29T11:54:27.612+0800 INFO [beat] instance/beat.go:992 Build info {"system_info": {"build": {"commit": "f79387d32717d79f689d94fda1ec80b2cf285d30", "libbeat": "7.8.0", "time": "2020-06-14T18:15:37.000Z", "version": "7.8.0"}}}
2020-07-29T11:54:27.612+0800 INFO [beat] instance/beat.go:995 Go runtime info {"system_info": {"go": {"os":"linux","arch":"amd64","max_procs":1,"version":"go1.13.10"}}}
2020-07-29T11:54:27.613+0800 INFO [beat] instance/beat.go:999 Host info {"system_info": {"host": {"architecture":"x86_64","boot_time":"2020-07-29T10:17:36+08:00","containerized":false,"name":"localhost.localdomain","ip":["127.0.0.1/8","::1/128","ip/24","fe80::a00:27ff:fef1:be56/64","10.0.0.5/8","fe80::a00:27ff:fe85:e7d4/64","ip/24"],"kernel_version":"4.14.35-1902.11.3.el7uek.x86_64","mac":["08:00:27:f1:be:56","08:00:27:85:e7:d4","52:54:00:43:f2:99","52:54:00:43:f2:99"],"os":{"family":"","platform":"ol","name":"Oracle Linux Server","version":"7.7","major":7,"minor":7,"patch":0},"timezone":"+08","timezone_offset_sec":28800,"id":"c53dd0074710bd4e8fc8d0354ca04621"}}}
2020-07-29T11:54:27.614+0800 INFO [beat] instance/beat.go:1028 Process info {"system_info": {"process": {"capabilities": {"inheritable":null,"permitted":["chown","dac_override","dac_read_search","fowner","fsetid","kill","setgid","setuid","setpcap","linux_immutable","net_bind_service","net_broadcast","net_admin","net_raw","ipc_lock","ipc_owner","sys_module","sys_rawio","sys_chroot","sys_ptrace","sys_pacct","sys_admin","sys_boot","sys_nice","sys_resource","sys_time","sys_tty_config","mknod","lease","audit_write","audit_control","setfcap","mac_override","mac_admin","syslog","wake_alarm","block_suspend","audit_read"],"effective":["chown","dac_override","dac_read_search","fowner","fsetid","kill","setgid","setuid","setpcap","linux_immutable","net_bind_service","net_broadcast","net_admin","net_raw","ipc_lock","ipc_owner","sys_module","sys_rawio","sys_chroot","sys_ptrace","sys_pacct","sys_admin","sys_boot","sys_nice","sys_resource","sys_time","sys_tty_config","mknod","lease","audit_write","audit_control","setfcap","mac_override","mac_admin","syslog","wake_alarm","block_suspend","audit_read"],"bounding":["chown","dac_override","dac_read_search","fowner","fsetid","kill","setgid","setuid","setpcap","linux_immutable","net_bind_service","net_broadcast","net_admin","net_raw","ipc_lock","ipc_owner","sys_module","sys_rawio","sys_chroot","sys_ptrace","sys_pacct","sys_admin","sys_boot","sys_nice","sys_resource","sys_time","sys_tty_config","mknod","lease","audit_write","audit_control","setfcap","mac_override","mac_admin","syslog","wake_alarm","block_suspend","audit_read"],"ambient":null}, "cwd": "/u01/filebeat/filebeat-7.8.0-linux-x86_64", "exe": "/u01/filebeat/filebeat-7.8.0-linux-x86_64/filebeat", "name": "filebeat", "pid": 4256, "ppid": 3025, "seccomp": {"mode":"filter","no_new_privs":true}, "start_time": "2020-07-29T11:54:23.640+0800"}}}
2020-07-29T11:54:27.614+0800 INFO instance/beat.go:310 Setup Beat: filebeat; Version: 7.8.0
2020-07-29T11:54:27.614+0800 INFO [index-management] idxmgmt/std.go:183 Set output.elasticsearch.index to 'filebeat-7.8.0' as ILM is enabled.
2020-07-29T11:54:27.615+0800 INFO eslegclient/connection.go:97 elasticsearch url: http://ip:9200
2020-07-29T11:54:27.615+0800 INFO [publisher] pipeline/module.go:113 Beat name: localhost.localdomain
2020-07-29T11:54:27.617+0800 INFO kibana/client.go:118 Kibana url: http://ip:5601
2020-07-29T11:54:27.618+0800 INFO [monitoring] log/log.go:118 Starting metrics logging every 30s
2020-07-29T11:54:28.538+0800 INFO kibana/client.go:118 Kibana url: http://ip:5601
2020-07-29T11:55:57.620+0800 INFO [monitoring] log/log.go:145 Non-zero metrics in the last 30s {"monitoring": {"metrics": {"beat":{"cpu":{"system":{"ticks":240,"time":{"ms":76}},"total":{"ticks":1690,"time":{"ms":273},"value":1690},"user":{"ticks":1450,"time":{"ms":197}}},"handles":{"limit":{"hard":65536,"soft":65536},"open":18},"info":{"ephemeral_id":"b51ce56d-6580-48d7-8bc1-78a936c23b3d","uptime":{"ms":93061}},"memstats":{"gc_next":15427008,"memory_alloc":8812392,"memory_total":128212928},"runtime":{"goroutines":168}},"filebeat":{"events":{"active":11,"added":25,"done":14},"harvester":{"files":{"82931d40-7cac-4415-a501-d4463f4306d7":{"last_event_published_time":"2020-07-29T11:55:49.712Z","last_event_timestamp":"2020-07-29T11:55:44.708Z","name":"/var/log/mysqld.log","read_offset":2166331,"size":2166026,"start_time":"2020-07-29T11:55:37.704Z"}},"open_files":1,"running":1,"started":1}},"libbeat":{"config":{"module":{"running":0},"reloads":1,"scans":1},"output":{"events":{"acked":2,"batches":2,"total":2}},"pipeline":{"clients":13,"events":{"active":0,"filtered":12,"published":2,"retry":1,"total":14},"queue":{"acked":2}}},"registrar":{"states":{"current":11,"update":14},"writes":{"success":14,"total":14}},"system":{"load":{"1":0.38,"15":0.79,"5":0.4,"norm":{"1":0.38,"15":0.79,"5":0.4}}}}}}
I have done as mentioned in filebeat.yml.
output.elasticsearch:
hosts: ["ip:9200"]
username: "elastic"
password: "password"
setup.kibana:
host: "ip:5601"
username: "elastic"
password: "password"
Am I missing anything in my configuration ? Anyone, please guide.
Thanks,
Grace