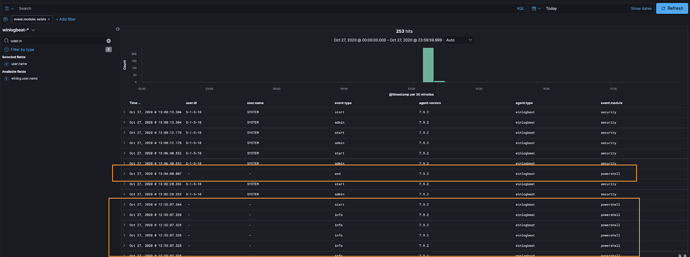
It doesn't appear that the powershell module for Winlogbeat 7.9.2 is recording the user.id or the user.name.
Is this intended or a bug?
One example:
{
"_index": "winlogbeat-7.9.2-2020.10.14-000001",
"_type": "_doc",
"_id": "Yjwza3UBFsYu-VWrDQYb",
"_version": 1,
"_score": null,
"_source": {
"@timestamp": "2020-10-27T17:55:07.344Z",
"message": "Engine state is changed from None to Available. \n\nDetails: \n\tNewEngineState=Available\n\tPreviousEngineState=None\n\n\tSequenceNumber=13\n\n\tHostName=ConsoleHost\n\tHostVersion=5.1.18362.1110\n\tHostId=c14b139b-215a-4f21-983c-e67106979c7c\n\tHostApplication=powershell.exe\n\tEngineVersion=5.1.18362.1110\n\tRunspaceId=98ad71a5-5237-41c2-ad32-24fdd088661f\n\tPipelineId=\n\tCommandName=\n\tCommandType=\n\tScriptName=\n\tCommandPath=\n\tCommandLine=",
"winlog": {
"channel": "Windows PowerShell",
"provider_name": "PowerShell",
"keywords": [
"Classic"
],
"opcode": "Info",
"computer_name": "[redacted]",
"event_id": 400,
"record_id": 690,
"task": "Engine Lifecycle",
"api": "wineventlog"
},
"host": {
"name": "[redacted]",
"os": {
"kernel": "10.0.18362.1139 (WinBuild.160101.0800)",
"build": "18363.1139",
"platform": "windows",
"version": "10.0",
"family": "windows",
"name": "Windows 10 Enterprise Evaluation"
},
"id": "9bdc5154-52ee-4763-8cab-1f6c670f34d9",
"ip": [
"fe80::81e2:50b5:eb1d:daf2",
"172.16.17.151"
],
"mac": [
"00:0c:29:b4:4c:e8"
],
"hostname": "[redacted]",
"architecture": "x86_64"
},
"log": {
"level": "information"
},
"powershell": {
"process": {
"executable_version": "5.1.18362.1110"
},
"engine": {
"new_state": "Available",
"previous_state": "None",
"version": "5.1.18362.1110"
},
"runspace_id": "98ad71a5-5237-41c2-ad32-24fdd088661f"
},
"event": {
"module": "powershell",
"category": [
"process"
],
"sequence": 13,
"action": "Engine Lifecycle",
"created": "2020-10-27T17:55:08.146Z",
"code": 400,
"type": [
"start"
],
"provider": "PowerShell",
"kind": "event"
},
"process": {
"entity_id": "c14b139b-215a-4f21-983c-e67106979c7c",
"command_line": "powershell.exe",
"title": "ConsoleHost",
"args": [
"powershell.exe"
],
"args_count": 1
},
"ecs": {
"version": "1.5.0"
},
"agent": {
"type": "winlogbeat",
"version": "7.9.2",
"hostname": "[redacted]",
"ephemeral_id": "2e280b70-00ef-4b00-bbd5-118feeab703a",
"id": "0c1c612e-b1cd-4a47-b9f9-28f811a29630",
"name": "[redacted]"
}
},
"fields": {
"@timestamp": [
"2020-10-27T17:55:07.344Z"
],
"event.created": [
"2020-10-27T17:55:08.146Z"
]
},
"sort": [
1603821307344
]
}