Hello,
I manage multiple isolated Elastic instances, on each I configured a Teams connector.
Now by default alerts in our Teams channel are pretty generic, for instance “Rule Spike in Logon Events from a Source IP generated 1 alerts”. They completely miss instance context by default.
What would be best practice or a good approach to enrich alerts with context.
I was thinking about just adding customer/instance tag to the rule name, i.e. “Rule Spike Logon [instance_xy]” manually. But I think this might not be possible for rules managed by Elastic.
What would be the best option in my situation?
Hello @Chickpea
Welcome to the Community!!
I am not sure if it is needed to edit the current Rule name by adding static instance id, if we check as part of {{context}} it captures the clusterName, can we try adding {{context.clusterName}} to the existing message. Also if needed Tag field can be also used to add the instance name & calling by {{rule.tags}}
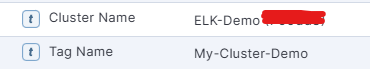
Thanks!!
1 Like
Thank you. In general a good approach that I would use. But it seems that security rules cannot access the Cluster Name since I don’t get any output when I put {{context.clusterName}} in my alert message.
However, I used {{{context.results_link}}} instead which provides a link to the alert which is also useful.
1 Like
