Hello there,
I'm using elastic-search, kibana and x-pack version 5.1.2, I'm using the native user-store.
I have two different aliases and templates:
$ cat irldf-campaign_manager_stats_template.json
{
"aliases": {
"irldf-campaign_stats": {}
},
"mappings": {
"campaign_stats": {
"properties": {
...
}
},
"template": "irldf-campaign_manager_stats-*"
}
$ cat irlh3-campaign_manager_stats_template.json
{
"aliases": {
"irlh3-campaign_stats": {}
},
"mappings": {
"campaign_stats": {
"properties": {
...
}
},
"template": "irlh3-campaign_manager_stats-*"
}
$ !1079
curl -XGET -u elastic 'localhost:9200/_cat/aliases?pretty';
Enter host password for user 'elastic':
irlh3-campaign_stats irlh3-campaign_manager_stats-test - - -
irldf-campaign_stats irldf-campaign_manager_stats-test - - -
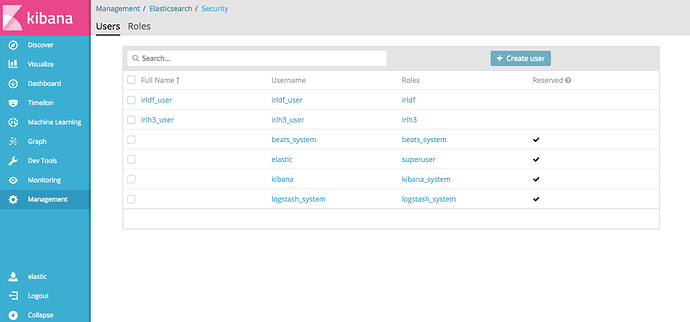
Then I've configured two roles associated with both aliases and assigned them to users:
$ curl -XGET 'localhost:9200/_xpack/security/role?pretty'
{
...
"irlh3" : {
"cluster" : [ ],
"indices" : [
{
"names" : [
"irlh3-campaign_stats"
],
"privileges" : [
"all"
]
},
{
"names" : [
".kibana*"
],
"privileges" : [
"manage",
"read",
"index"
]
},
{
"names" : [
".reporting*"
],
"privileges" : [
"manage",
"read",
"index"
]
}
],
"run_as" : [ ],
"metadata" : { }
},
"irldf" : {
"cluster" : [ ],
"indices" : [
{
"names" : [
"irldf-campaign_stats"
],
"privileges" : [
"all"
]
},
{
"names" : [
".kibana*"
],
"privileges" : [
"manage",
"read",
"index"
]
},
{
"names" : [
".reporting*"
],
"privileges" : [
"manage",
"read",
"index"
]
}
],
"run_as" : [ ],
"metadata" : { }
}
}
$ curl -XGET 'localhost:9200/_xpack/security/user/irldf_user?pretty';
{
"irldf_user" : {
"username" : "irldf_user",
"roles" : [
"irldf",
"kibana_user",
"reporting_user"
],
"full_name" : "IRLDF User",
"email" : "xrldf@anony.mous",
"metadata" : { },
"enabled" : true
}
}
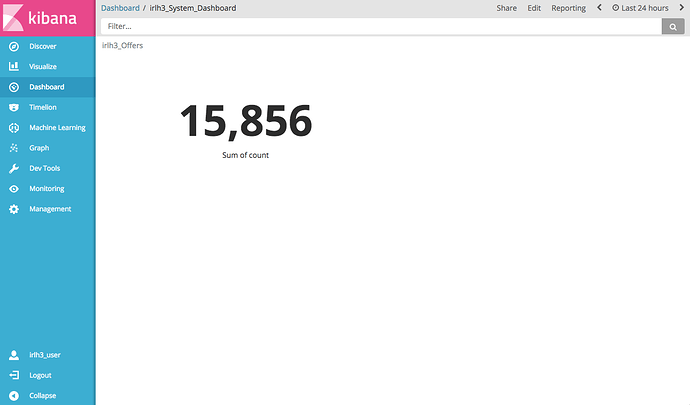
In kibana I create two visualization, one on each alias, and I put each visualization in separate dashboards. However, if I log into kibana with say the irldf_user I can still see the data from both visualizations in both dashboards. That is, the authorization is not working as I expected? Did I make a mistake settings this up? I'm implementing a separate index per user model.