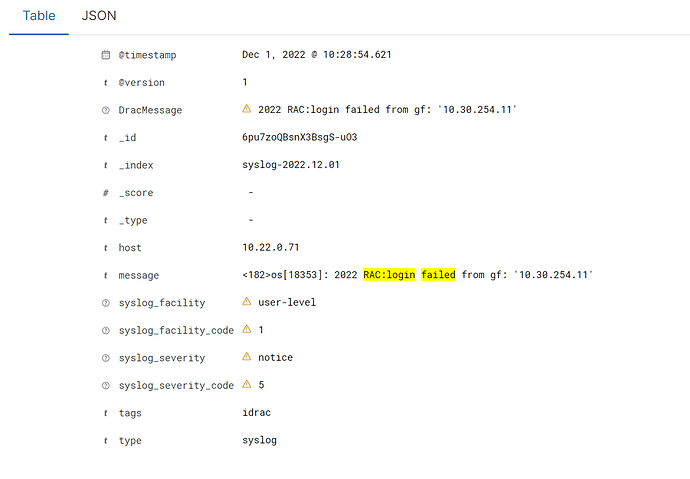
I am looking for help to grok Syslog from Dell idrac I am having problems taking the grok below and making it work with a Logstash. Your help is deeply appreciated!
Extracting additional fields from iDRAC logs I found online.
<Exec>
parse_syslog();
if $Message =~ /(?x)^([a-zA-Z]*),\ Category:\ ([a-zA-Z]*),
\ MessageID:\ ([a-zA-Z0-9]*),\ Message:\ (.*)$/
{
$DracMsgLevel = $1;
$DracMscCategory = $2;
$DracMscID = $3;
$DracMessage = $4;
}
</Exec>
My logstash conf
input {
udp {
port => "514"
type => "syslog"
}
}
filter {
if [type] == "syslog" {
}
if [host] == '101' {
mutate {
add_tag => ["idrac"]
}
grok { # Match syslog data and add fields
match => { "message" => "%{SYSLOGTIMESTAMP:syslog_timestamp} %{SYSLOGHOST:syslog_hostname} %{DATA:syslog_program}(?:\[%{POSINT:syslog_pid}\])?: %{GREEDYDATA:syslog_message}" }
add_field => [ "received_at", "%{@timestamp}" ]
add_field => [ "received_from", "%{host}" ]
}
date { # Match date in syslog message and set timestamp field to this
match => [ "syslog_timestamp", "MMM d HH:mm:ss", "MMM dd HH:mm:ss" ]
target => "syslog_timestamp"
}
}
}