Hello,
I'm noticing a large amount of detections on the "Unusual Parent-Child Relationship" detection rule whichs seems to be related to the fact that some processes don't have a parent process. Data source are sysmon forwarded events.
The query which looks like this:
signal.rule.query: "event.category:process and event.type:(start or process_started) and process.parent.executable:* and (
process.parent.name:autochk.exe and not process.name:(chkdsk.exe or doskey.exe or WerFault.exe) or
process.parent.name:smss.exe and not process.name:(autochk.exe or smss.exe or csrss.exe or wininit.exe or winlogon.exe or WerFault.exe) or
process.name:autochk.exe and not process.parent.name:smss.exe or process.name:(fontdrvhost.exe or dwm.exe) and not process.parent.name:(wininit.exe or winlogon.exe) or
process.name:(consent.exe or RuntimeBroker.exe or TiWorker.exe) and not process.parent.name:svchost.exe or
process.name:wermgr.exe and not process.parent.name:(svchost.exe or TiWorker.exe) or
process.name:SearchIndexer.exe and not process.parent.name:services.exe or
process.name:SearchProtocolHost.exe and not process.parent.name:(SearchIndexer.exe or dllhost.exe) or
process.name:dllhost.exe and not process.parent.name:(services.exe or svchost.exe) or
process.name:smss.exe and not process.parent.name:(System or smss.exe) or
process.name:csrss.exe and not process.parent.name:(smss.exe or svchost.exe) or
process.name:wininit.exe and not process.parent.name:smss.exe or
process.name:winlogon.exe and not process.parent.name:smss.exe or
process.name:(lsass.exe or LsaIso.exe) and not process.parent.name:wininit.exe or
process.name:LogonUI.exe and not process.parent.name:(wininit.exe or winlogon.exe) or
process.name:services.exe and not process.parent.name:wininit.exe or
process.name:svchost.exe and not process.parent.name:(MsMpEng.exe or services.exe) or
process.name:spoolsv.exe and not process.parent.name:services.exe or
process.name:taskhost.exe and not process.parent.name:(services.exe or svchost.exe) or
process.name:taskhostw.exe and not process.parent.name:(services.exe or svchost.exe) or
process.name:userinit.exe and not process.parent.name:(dwm.exe or winlogon.exe)
)"
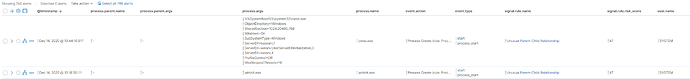
Is looking for events where process.parent.executable:*. But processes which don't have a parent process have a hyphen as value.
For example:
So am I correct thinking that the query should be updated so that it ignore events where process.parent.executable : "-"?
For example:
event.category:process and event.type:(start or process_started) and process.parent.executable:* and not process.parent.executable:"-" and ...
Or am I missing something?
Grtz
Willem