Hello everyone,
I’m opening this topic because I couldn’t find any solution or open issue related to this problem, either in GitHub or other forums.
We are currently using Elastic Security as our SIEM, and one of our most relevant use cases is detecting data exfiltration to USB devices.
By default, the Elastic Defend integration logs file writes and deletions to removable drives, using the field:
file.Ext.device.bus_type:"Usb"
The logs also include additional USB device information, such as:
-
file.Ext.device.product_id
-
file.Ext.device.serial_number
-
file.Ext.device.vendor_id
However, the most important field — file.Ext.device.serial_number — is always logged as either a random number or simply 0.
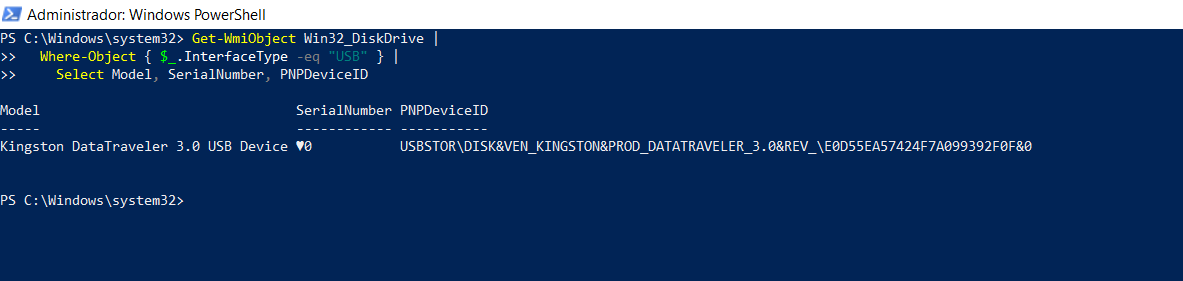
For example, with a Kingston USB drive we tested:
file.Ext.device.product_id: DataTraveler 3.0
file.Ext.device.serial_number: 0
file.Ext.device.vendor_id: Kingston
But the real serial number, which can be retrieved from the Windows Registry key USBSTOR, is something like:
E0D55E62C799176068XXXXX
This discrepancy makes it very hard to reliably track specific devices.
Has anyone else experienced this issue?
Is this a known bug or a current limitation?
Is the Elastic engineering team aware of it / working on a fix?
Any ideas, workarounds, or official confirmation would be greatly appreciated.
Thanks in advance,
Best regards