First let me start by explaining what i am trying to achieve. I have a cluster of 3 nodes (kibana is also installed on the same VM with one of the nodes) -each of 3 nodes have all the roles- with mutual TLS between cluster nodes and kibana. I want to add two new VMs to this setup. One acting as both fleet-server(If im not mistaken, to be exact acting as both elastic-agent and fleet-server) and the other one acting as elastic-agnet only, with mutual TLS active on all possible connections.
To give an overview of how is the current set-up of mutual TLS. First, using elasticsearch cert-util i created a self-singed certificat:
ca.crtca.key
Then i used it to generate all other certificates.
About steps i took to install fleet-server:
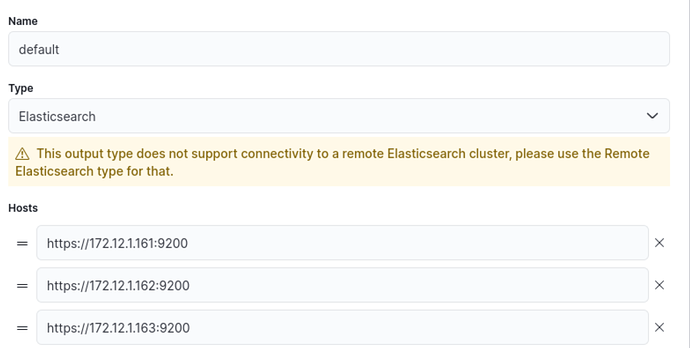
first i modified my output to point to my nodes like below. I know there is more to config in this section and im gonna get back to it later, i have tried multiple solutions that did not work.
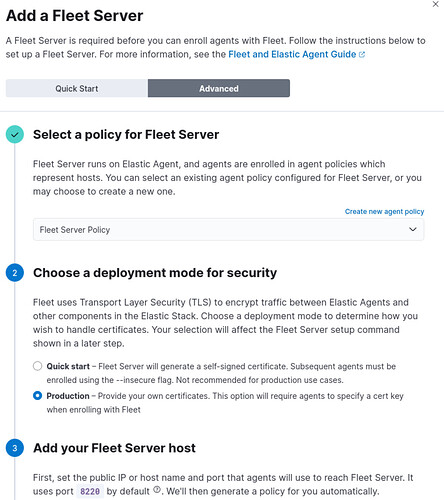
then using automatically generate policy
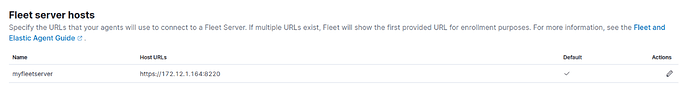
and specifying flee-server url
and then adding server with generating token following section below:
i tried to install the tar file with the command below:
--url=https://172.12.1.164:8220
--fleet-server-port=8220
--fleet-server-es=https://172.12.1.161:9200
--fleet-server-es-ca=/tmp/ca.crt
--fleet-server-es-cert=/tmp/fleet-server/fleet-server.crt
--fleet-server-es-cert-key=/tmp/fleet-server/fleet-server.key
--fleet-server-service-token=AAEAAWVsYXN0aWMvZmxlZXQtc2VydmVyL3Rva2VuLTE3NTM2MTM1NjEyMzQ6bmJ6dHpRNlpUWmFCZXZ6T09sRmRkQQ
--fleet-server-policy=fleet-server-policy
--fleet-server-cert=/tmp/fleet-server/fleet-server.crt
--fleet-server-cert-key=/tmp/fleet-server/fleet-server.key
--fleet-server-client-auth=required
--certificate-authorities=/tmp/ca.crt
--elastic-agent-cert=/tmp/fleet-server/fleet-server.crt
--elastic-agent-cert-key=/tmp/fleet-server/fleet-server.key
Im going to explain why i chose this set of parameters for installation. Maybe i just misunderstood the whole thing:
--url=https://172.12.1.164:8220 : To specify the IP and port which fleet-server will be avialbale on.
--fleet-server-port=8220 : To specify the port which fleet-server will be available on. I don't know if it is necessary considering port is specified in --url=https but did it anyway just in case.
--fleet-server-es=https://172.12.1.161:9200: Here is the how flee-server will connect to the cluster for reading and storing its data. Although probably it would be better to list other nodes but i did not know it would accept a list or not so i just added one node.
--fleet-server-es-ca=/tmp/ca.crt: This the original self-signed ca i used for generating all other CAs. I added this so when elasticsearch present a cert to fleet-sever it could verify the cert with this ca. Did i understand this parameter right?
--fleet-server-es-cert=/tmp/fleet-server/fleet-server.crt: This is the certificate flee-server (by fleet-server i mean the fleet-server subprocess of elastic-agent) present to elasticsearch for mutual TLS.
--fleet-server-es-cert-key=/tmp/fleet-server/fleet-server.key: The key for the --fleet-server-es-cert.
--fleet-server-service-token=AAEAAWVsYXN0aWMv: This is the token which fleet-server will use for authenticating itself to the cluster.
--fleet-server-policy=fleet-server-policy: The policy which will be applied to elastic-agent which is the automatically generated policy and will cause the fleet-server subprocess to be run and make the elastic-agent act as a fleet-server.
--fleet-server-cert=/tmp/fleet-server/fleet-server.crt: This is the certificate fleet-server will present to clients like elastic-agent which will try to connect to fleet-server.
Im using the same cert for both connections: fleet-server to elasticsearch cluster and flee-server to elastic-agents.
--fleet-server-cert-key=/tmp/fleet-server/fleet-server.key: The key for the previous parameter.
--fleet-server-client-auth=required : This specify that connection to fleet-server must use mutual TLS so it is mandatory for elastic-agent trying to connect to fleet-server present a certificate.
--certificate-authorities=/tmp/ca.crt: This is the same self-signed certificate used to generate all other certs.
Here my understanding is a fleet server can be seen as two parts (elastic-agent + fleet subprocess) So each of these components use --certificate-authorities=/tmp/ca.crt to verify certificate presented to them. I am not sure if understood it right?
--elastic-agent-cert=/tmp/fleet-server/fleet-server.crt: This for elastic-agent part of fleet-sever when trying to communicate withe fleet-server. this is based on assumption of fleet-server being two parts (elastic-agent + fleet subprocess).
--elastic-agent-cert-key=/tmp/fleet-server/fleet-server.key: Key for the previous parameter.
It is worth mentioning that all certs are generated with no password
I guess the most important question here is did i select the right set of parameters and did i understand them right?
Following the steps above the fleet server will be connected and have a healthy state. But when i check the logs in /opt/Elastic/Agent/data/elastic-agent-*/logs/elastic-agent.ndjson. There are errors related to agent consecutively
trying to connect to 3 cluster nodes but failing. I believe the problem must be related to output
And i tried different methods and i faced different errors. Like when i use ca.crt fingerprint
i get errors of not including certificate chain which i tried solving it with this answer but did not work. Then i tried not using fingerprint and instead using the yaml
section like this which provide the path to the self signed ca orpassing it directly like this answer but still did no work. Am i doing something totally wrong? Can someone please provide some general guidance on how to set this?
By the way this is all done on elasticsearch version 8.17.