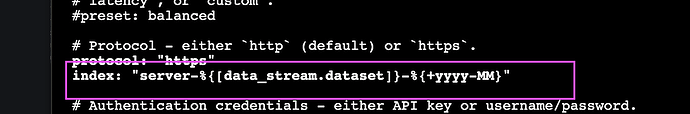
I have read through many articles and am not able to solve this issue for me. I’m trying to generate a new api key that has rights over creating indicies using filebeat. I have tried doing this through the superuser account but per the below post, it is not an option anymore so I created a new account with no roles and just an api key with the proper permissions but still getting the error
this action is granted by the index privileges [auto_configure,create_index,manage,all]"}, dropping event!"
Below is the configuration I used to grant permissions for a a different user beside the default elastic user
POST /_security/api_key
{
"name": "test-key",
"role_descriptors": {
"filebeat_writer": {
"cluster": ["monitor", "read_ilm", "read_pipeline"],
"index": [
{
"names": ["*-*"],
"privileges": ["auto_configure","create_index","manage","all"]
}
]
}
}
}
Any help is appreciated as I have been trying to solve this for a few weeks now.