Hello all,
We really like the Kibana List API. it enables us to make black and whitelists we can use in Elastic detection rules. For example a list of developers, compromised accounts, vpn users, etc. We also really like the ability to add metadata to the values in the list.
But atm the Kibana List API is only decently usable with a tool such as Insomnia or Postman, as the Kibana API is not accessible through Dev Tools and there is no gui to manage the Kibana Lists.
Some questions:
-
Are there any plans to make gui to manage Kibana Lists?
-
If I remember correctly there already is a feature request to make the Kibana API accessible through Dev Tools. Wondering what the status is.. (anyone finds the related GH issue?)
-
Are there any plans to merge the Kibana Lists and the ML Filter Lists, which are actually very similar (although the latter seems to lack API?)?
-
As we added metadata to some of our list items, we need these fields to be mapped correctly. I'm not sure how do this, considering these are 'system indices" starting with a '.'? For example:
An item we are adding:
{
"list_id": "list-user-name-compromised-2021",
"value": "user.name",
"meta": {
"comment": "Nigeria",
"heat_incident_number": "22771",
"heat_incident_source": "Avanan",
"user_email": "User.Name@domain.com",
"user_name_format": "firstname.lastname"
}
}
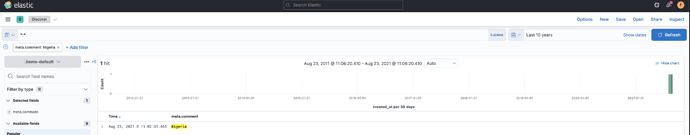
But Searching for the list items in discover show the meta fields as unmapped:
Any supported way to make sure these get the correct mapping? What template would we need to edit and how do I apply this template on the .items-default-* indices?
Thanks!
Willem