Hi there,
I have 90 days worth of windows event logs (partitioned per day) and a set of rules that I want to apply on those days.
I noticed that when I activate a rule it can only go forward in time, is there a way to effectively replay the rule on past historical events to generate the alerts on each of the days?
This is for a SOC blue team exercise to monitor the team performance when triaging events.
The only option I see is to sort of copy and paste old events as if they were new, but this will be a massive job on the order of TB size.
Any help is appreciated!
Hi @priamai! Thanks for your question. There are 2 options I can think of...
-
set a really long look-back interval on the rule ... this could be problematic for a number of reasons and won't work for all rule types, but it could be a possibility. You could easily run into performance problems and/or hit your maxSignals limit.
-
use a timestamp override. If your data has
event.ingestedand it was imported recently, that might be an option. Otherwise, if you don't have another more recent timestamp available on the events, you may need to take the approach from your original question (rewrite the events with a more recent timestamp, either using the@timestampfield or a new override field).
There has been talk about adding more explicit support for this type of thing, but as far as I know, it hasn't yet been prioritized. In the meantime, one of the above may have to suffice (I wonder if runtime fields could be another option, combined with a timestamp override?)
Hope this helps!
Madi
I just thought of a third option, let me know if this is possible:
- run the rule queries with my client code
- emulate the output of the alert in the correct index
I could not find any information about how ES manages the indexes related to the Detection engine.
Are there any documents I could look into?
Otherwise I can generate a few events with your approach such as (2) and then figure out the index alert structure?
Cheers.
Why don't you just perform Adversary emulation and generate fresh detections?
Yes we do that already (with redcanary and other commercial BAS) for training purposes of new SOC analysts, but for this particular exercise we do have already historical data with known incidents that we want replay together with baseline (attack free) events.
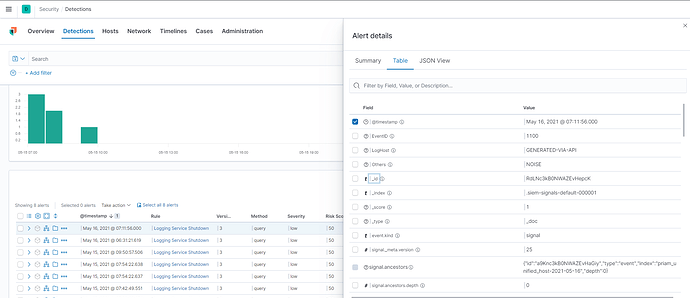
So I have been doing some experiments and there is indeed an hidden index called: .siem-signals-default-*****
which contains the the event that triggered and the rule relationships in the signal document.
It seems not a big deal to write an injector for that but any documentation on that index is welcome.
Cheers.
If you really need too then:
- Stop filebeat and logstash.
- Clear old data from Elasticsearch if there.
- Delete registry files
registryandregistry.old. - Run logstash.
- Run filebeat using command
filebeat -e -once.
Yeah but for the historical data is more than 5TB of streamed logs and we don't keep the original evt files or similar for filebeat to replay.
I managed to butcher a solution and generate an alert directly into the index, is working but not elegant.
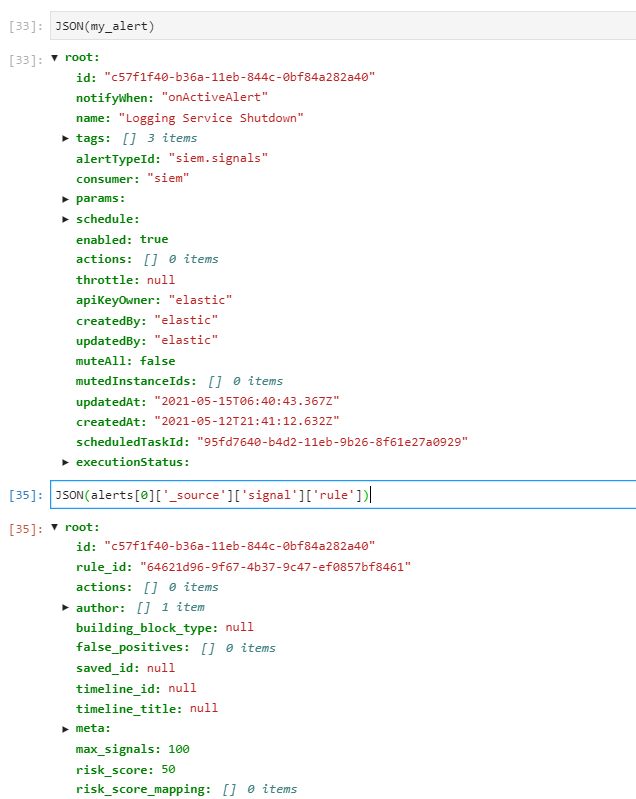
What I discovered is that the rule object nested inside the alert is not identical to the rule object you get from the kibana api.
The one from the API has very few fields compared to what is inside the siem index.
For now I do like this:
- for each rule
- generate 1 trigger event from the past
- copy the rule object from the test event
- add the new event information
@priamai Which APIs are you using? Can you just use the source data from the index?
Is this a workable solution for you in the meantime?
This topic was automatically closed 28 days after the last reply. New replies are no longer allowed.