No. You need to create specific roles that have the privileges that are required for the given space. See our documentation
Can you clarify what you mean by this?
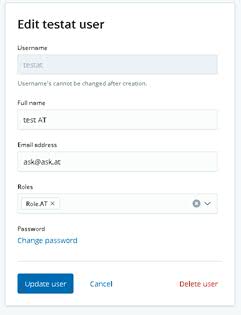
You cannot use role as a field in role mapping rules ( this part: { "field": { "role": "Role.AT" } }). Role mapping rules assign roles to users based on some other properties, if the user had the role already, you wouldn't need a role mapping rule to assign the role to the user. Please read through our documentation here and here again, I'm certain it will be beneficial for you.
Yes.
I can only assume that because your role mapping or the SAML attribute mapping is wrong, the user doesn't get the necessary roles when logging in via SAML.
- What is the value for
attributes.groups:in your configuration? - Does the user belong to the group
Role.ATin your SAML IDP or the underlying LDAP? - Please enable trace logging for the SAML Realm as described in our troubleshooting docs and review the logs. We are printing out helpful information for debugging there. If you still can't make sense of it, please share the relevant parts here so that we can take a look
Hope this helps