which configuration schemes are avaliable in 8.8 version of slatic clusterization?
Hello,
It is not clear what you are asking, can you provide some context? What do you mean by Configuration Schemes?
im talking about bootstrap configuration scheme is avaliable at 8.8 version in elastic because only configuration that works for me is single node scheme configuration with token system to adding nodes
i mean multinode with discovery it is avaliable? in 8.8?
Yes, there is no change on this.
How are you running Elasticsearch and how are you trying to add new nodes? What kind of error are you getting?
Single-node should be used only for tests purposes, it is not recommended for production.
The way to configure a production cluster with multiple nodes will change depending on how you are running it, but the configuration is basically the same.
A couple of time ago I wrote a small blog post on how to configure a 3-node cluster with security enable using version 8, this uses Virtual Machines and you can read it here, maybe it help you to understand what needs to be configured.
that's great i have to configure 3 masternodes and 4 data nodes there.i will follow that blog.
hi, again i got this error [2023-07-13T11:40:32,117][ERROR][o.e.b.Elasticsearch ] [Nodo1] fatal exception while booting Elasticsearch
org.elasticsearch.ElasticsearchSecurityException: failed to load SSL configuration [xpack.security.transport.ssl] - cannot load PEM private key from [/etc/elasticsearch/certs/Nodo1/Nodo1.key] due to BadPading
i check to see if it was a certificate permissions problem but
I followed the steps of the blog 1 by 1
Never saw this error, please share the entire error log as plain text, not as screenshot.
Use the preformatted text option, the </> button. Also, share your elasticsearch.yml.
Something is not right or you wouldn't get this error. Did you set a passphrase for the certificates? Did you added the correct passphrase to the elasticsearch keystore?
i did not set any phrase
[2023-07-13T11:40:32,117][ERROR][o.e.b.Elasticsearch ] [Nodo1] fatal exception while booting Elasticsearch
org.elasticsearch.ElasticsearchSecurityException: failed to load SSL configuration [xpack.security.transport.ssl] - cannot load PEM private key from [/etc/elasticsearch/certs/Nodo1/Nodo1.key] due to BadPad$
at org.elasticsearch.xpack.core.ssl.SSLService.lambda$loadSslConfigurations$11(SSLService.java:617) ~[?:?]
at java.util.HashMap.forEach(HashMap.java:1429) ~[?:?]
at java.util.Collections$UnmodifiableMap.forEach(Collections.java:1553) ~[?:?]
at org.elasticsearch.xpack.core.ssl.SSLService.loadSslConfigurations(SSLService.java:613) ~[?:?]
at org.elasticsearch.xpack.core.ssl.SSLService.<init>(SSLService.java:159) ~[?:?]
at org.elasticsearch.xpack.core.XPackPlugin.createSSLService(XPackPlugin.java:498) ~[?:?]
at org.elasticsearch.xpack.core.XPackPlugin.createComponents(XPackPlugin.java:326) ~[?:?]
at org.elasticsearch.node.Node.lambda$new$16(Node.java:726) ~[elasticsearch-8.8.2.jar:?]
at org.elasticsearch.plugins.PluginsService.lambda$flatMap$2(PluginsService.java:266) ~[elasticsearch-8.8.2.jar:?]
at java.util.stream.ReferencePipeline$7$1.accept(ReferencePipeline.java:273) ~[?:?]
at java.util.stream.ReferencePipeline$3$1.accept(ReferencePipeline.java:197) ~[?:?]
at java.util.AbstractList$RandomAccessSpliterator.forEachRemaining(AbstractList.java:722) ~[?:?]
at java.util.stream.AbstractPipeline.copyInto(AbstractPipeline.java:509) ~[?:?]
at java.util.stream.AbstractPipeline.wrapAndCopyInto(AbstractPipeline.java:499) ~[?:?]
at java.util.stream.AbstractPipeline.evaluate(AbstractPipeline.java:575) ~[?:?]
at java.util.stream.AbstractPipeline.evaluateToArrayNode(AbstractPipeline.java:260) ~[?:?]
at java.util.stream.ReferencePipeline.toArray(ReferencePipeline.java:616) ~[?:?]
at java.util.stream.ReferencePipeline.toArray(ReferencePipeline.java:622) ~[?:?]
at java.util.stream.ReferencePipeline.toList(ReferencePipeline.java:627) ~[?:?]
at org.elasticsearch.node.Node.<init>(Node.java:741) ~[elasticsearch-8.8.2.jar:?]
at org.elasticsearch.node.Node.<init>(Node.java:327) ~[elasticsearch-8.8.2.jar:?]
at org.elasticsearch.bootstrap.Elasticsearch$2.<init>(Elasticsearch.java:216) ~[elasticsearch-8.8.2.jar:?]
at org.elasticsearch.bootstrap.Elasticsearch.initPhase3(Elasticsearch.java:216) ~[elasticsearch-8.8.2.jar:?]
at org.elasticsearch.bootstrap.Elasticsearch.main(Elasticsearch.java:67) ~[elasticsearch-8.8.2.jar:?]
Caused by: org.elasticsearch.common.ssl.SslConfigException: cannot load PEM private key from [/etc/elasticsearch/certs/Nodo1/Nodo1.key] due to BadPaddingException (Given final block not properly padded. Su$
at org.elasticsearch.common.ssl.SslFileUtil.securityException(SslFileUtil.java:115) ~[?:?]
In the example on post I've shared in a previous answer you would need to create the certificate authority and node certificates using a passphrase for imprved security, then you would need to add this passphrase to the elasticsearch keystore.
If you didn't created any passphrase them you missed some steps.
If you do not want to use a passphrase you will need to adapt the commands mentioned on the example to not use it, basically do not use the --pass parameter.
The error you shared is probably related to this.
now it works but then it throws this error ! the elastic is up but could not comunicate while curl to the url trow this at the log
[2023-07-13T14:13:52,314][WARN ][o.e.h.AbstractHttpServerTransport] [Nodo1] caught exception while handling client http traffic, closing connection Netty4HttpChannel{localAddress=/192.168.100.84:9200, remo$
io.netty.handler.codec.DecoderException: javax.net.ssl.SSLHandshakeException: Received fatal alert: bad_certificate
at io.netty.handler.codec.ByteToMessageDecoder.callDecode(ByteToMessageDecoder.java:499) ~[?:?]
at io.netty.handler.codec.ByteToMessageDecoder.channelRead(ByteToMessageDecoder.java:290) ~[?:?]
at io.netty.channel.AbstractChannelHandlerContext.invokeChannelRead(AbstractChannelHandlerContext.java:444) ~[?:?]
at io.netty.channel.AbstractChannelHandlerContext.invokeChannelRead(AbstractChannelHandlerContext.java:420) ~[?:?]
at io.netty.channel.AbstractChannelHandlerContext.fireChannelRead(AbstractChannelHandlerContext.java:412) ~[?:?]
at io.netty.channel.DefaultChannelPipeline$HeadContext.channelRead(DefaultChannelPipeline.java:1410) ~[?:?]
at io.netty.channel.AbstractChannelHandlerContext.invokeChannelRead(AbstractChannelHandlerContext.java:440) ~[?:?]
at io.netty.channel.AbstractChannelHandlerContext.invokeChannelRead(AbstractChannelHandlerContext.java:420) ~[?:?]
at io.netty.channel.DefaultChannelPipeline.fireChannelRead(DefaultChannelPipeline.java:919) ~[?:?]
at io.netty.channel.nio.AbstractNioByteChannel$NioByteUnsafe.read(AbstractNioByteChannel.java:166) ~[?:?]
at io.netty.channel.nio.NioEventLoop.processSelectedKey(NioEventLoop.java:788) ~[?:?]
at io.netty.channel.nio.NioEventLoop.processSelectedKeysPlain(NioEventLoop.java:689) ~[?:?]
at io.netty.channel.nio.NioEventLoop.processSelectedKeys(NioEventLoop.java:652) ~[?:?]
at io.netty.channel.nio.NioEventLoop.run(NioEventLoop.java:562) ~[?:?]
at io.netty.util.concurrent.SingleThreadEventExecutor$4.run(SingleThreadEventExecutor.java:997) ~[?:?]
at io.netty.util.internal.ThreadExecutorMap$2.run(ThreadExecutorMap.java:74) ~[?:?]
at java.lang.Thread.run(Thread.java:1623) ~[?:?]
Caused by: javax.net.ssl.SSLHandshakeException: Received fatal alert: bad_certificate
at sun.security.ssl.Alert.createSSLException(Alert.java:130) ~[?:?]
at sun.security.ssl.Alert.createSSLException(Alert.java:117) ~[?:?]
at sun.security.ssl.TransportContext.fatal(TransportContext.java:365) ~[?:?]
at sun.security.ssl.Alert$AlertConsumer.consume(Alert.java:287) ~[?:?]
at sun.security.ssl.TransportContext.dispatch(TransportContext.java:204) ~[?:?]
at sun.security.ssl.SSLTransport.decode(SSLTransport.java:172) ~[?:?]
at sun.security.ssl.SSLEngineImpl.decode(SSLEngineImpl.java:736) ~[?:?]
at sun.security.ssl.SSLEngineImpl.readRecord(SSLEngineImpl.java:691) ~[?:?]
at sun.security.ssl.SSLEngineImpl.unwrap(SSLEngineImpl.java:506) ~[?:?]
at sun.security.ssl.SSLEngineImpl.unwrap(SSLEngineImpl.java:482) ~[?:?]
at javax.net.ssl.SSLEngine.unwrap(SSLEngine.java:679) ~[?:?]
at io.netty.handler.ssl.SslHandler$SslEngineType$3.unwrap(SslHandler.java:297) ~[?:?]
at io.netty.handler.ssl.SslHandler.unwrap(SslHandler.java:1352) ~[?:?]
at io.netty.handler.ssl.SslHandler.decodeJdkCompatible(SslHandler.java:1245) ~[?:?]
at io.netty.handler.ssl.SslHandler.decode(SslHandler.java:1294) ~[?:?]
at io.netty.handler.codec.ByteToMessageDecoder.decodeRemovalReentryProtection(ByteToMessageDecoder.java:529) ~[?:?]
at io.netty.handler.codec.ByteToMessageDecoder.callDecode(ByteToMessageDecoder.java:468) ~[?:?]
Thank you so much you nailed to solve my problem you r brilliant ![]()
![]()
This is my configuration yml to set 2 nodes as master how would i have to change? or what to add beacuse i set the option node.master: true but it didnt work, and also add the line node.roles: [master]
path.data: /var/lib/elasticsearch
path.logs: /var/log/elasticsearch
bootstrap.memory_lock: true
cluster.name: Cluster
node.name: Nodo1
network.host: ['192.168.100.84']
http.port: 9200
cluster.initial_master_nodes: ['192.168.100.84', '192.168.100.82']
discovery.seed_hosts: ['192.168.100.84', '192.168.100.82', '192.168.100.81']
# security settings
xpack.security.enabled: true
xpack.security.autoconfiguration.enabled: false
# transport ssl
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.key: certs/Nodo1/Nodo1.key
xpack.security.transport.ssl.certificate: certs/Nodo1/Nodo1.crt
xpack.security.transport.ssl.certificate_authorities: certs/ca/ca.crt
## http ssl
xpack.security.http.ssl.enabled: true
xpack.security.http.ssl.key: certs/Nodo1/Nodo1.key
xpack.security.http.ssl.certificate: certs/Nodo1/Nodo1.crt
xpack.security.http.ssl.certificate_authorities: certs/ca/ca.crt
It is not clear what you want to change and what didn't work.
This example does not specify any role, so every node will have all the roles.
If you want to have dedicated master nodes you will need to set node.roles: [ master ], but you will need to have data nodes in your cluster as well with node.roles: [ data ] to exclusive data nodes.
i've got an erro while using or set one the elastic nodes to master.
this is my node 2 configuration as a node master
path.data: /var/lib/elasticsearch
path.logs: /var/log/elasticsearch
bootstrap.memory_lock: true
cluster.name: Cluster
node.name: Nodo2
node.roles: [ master ]
network.host: ['192.168.100.82']
http.port: 9200
cluster.initial_master_nodes: ['192.168.100.84', '192.168.100.82']
discovery.seed_hosts: ['192.168.100.84', '192.168.100.82', '192.168.100.81']
# security settings
xpack.security.enabled: true
xpack.security.autoconfiguration.enabled: false
# transport ssl
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.key: certs/Nodo2/Nodo2.key
xpack.security.transport.ssl.certificate: certs/Nodo2/Nodo2.crt
xpack.security.transport.ssl.certificate_authorities: certs/ca/ca.crt
## http ssl
xpack.security.http.ssl.enabled: true
xpack.security.http.ssl.key: certs/Nodo2/Nodo2.key
xpack.security.http.ssl.certificate: certs/Nodo2/Nodo2.crt
xpack.security.http.ssl.certificate_authorities: certs/ca/ca.crt
and this my node 1 configuration as a master
path.data: /var/lib/elasticsearch
path.logs: /var/log/elasticsearch
bootstrap.memory_lock: true
cluster.name: Cluster
node.name: Nodo1
node.roles: [ master ]
network.host: ['192.168.100.84']
http.port: 9200
cluster.initial_master_nodes: ['192.168.100.84', '192.168.100.82']
discovery.seed_hosts: ['192.168.100.84', '192.168.100.82', '192.168.100.81']
# security settings
xpack.security.enabled: true
xpack.security.autoconfiguration.enabled: false
# transport ssl
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.key: certs/Nodo1/Nodo1.key
xpack.security.transport.ssl.certificate: certs/Nodo1/Nodo1.crt
xpack.security.transport.ssl.certificate_authorities: certs/ca/ca.crt
## http ssl
xpack.security.http.ssl.enabled: true
xpack.security.http.ssl.key: certs/Nodo1/Nodo1.key
xpack.security.http.ssl.certificate: certs/Nodo1/Nodo1.crt
xpack.security.http.ssl.certificate_authorities: certs/ca/ca.crt
and this this the node 3 config to data node
path.data: /var/lib/elasticsearch
path.logs: /var/log/elasticsearch
bootstrap.memory_lock: true
cluster.name: Cluster
node.name: Nodo3
node.roles: [ data ]
network.host: ['192.168.100.81']
http.port: 9200
cluster.initial_master_nodes: ['192.168.100.84', '192.168.100.82']
discovery.seed_hosts: ['192.168.100.84', '192.168.100.82', '192.168.100.81']
# security settings
xpack.security.enabled: true
xpack.security.autoconfiguration.enabled: false
# transport ssl
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.key: certs/Nodo3/Nodo3.key
xpack.security.transport.ssl.certificate: certs/Nodo3/Nodo3.crt
xpack.security.transport.ssl.certificate_authorities: certs/ca/ca.crt
## http ssl
xpack.security.http.ssl.enabled: true
xpack.security.http.ssl.key: certs/Nodo3/Nodo3.key
xpack.security.http.ssl.certificate: certs/Nodo3/Nodo3.crt
xpack.security.http.ssl.certificate_authorities: certs/ca/ca.crt
This is expected, only one node will be the active master.
Also, to have resiliency you need at least three master eligible nodes, you only have two, so if your master goes down, your entire cluster will go down.
And the discovery.seed_hosts needs to have only the master eligible nodes.
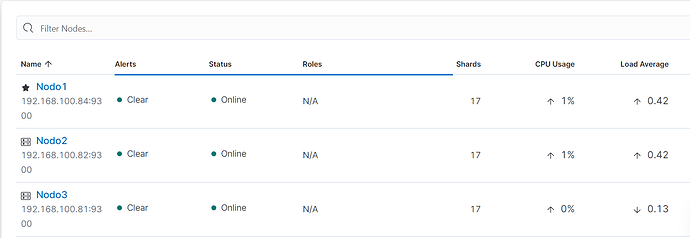
thank you sifu (master) you help me al lot, i have sucessfully start up my production cluster