Hello everyone, I need some help regarding what's going on
I setup my Elasticsearch + fleet server + kibana with a ubuntu machine.
I added a windows machine with elastic agent. (Interation ElasticDefend => I can see all logs)
Now when i try to "windows" or "system" integration to the agent. I don't see any logs related to these 2 (I have sysmon installed and running and I confirmed in event viewer that logs exists)
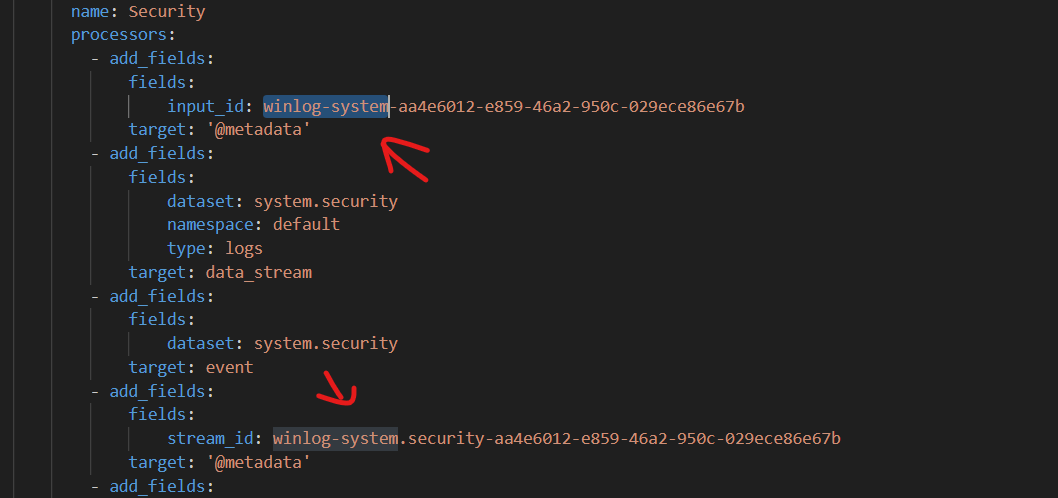
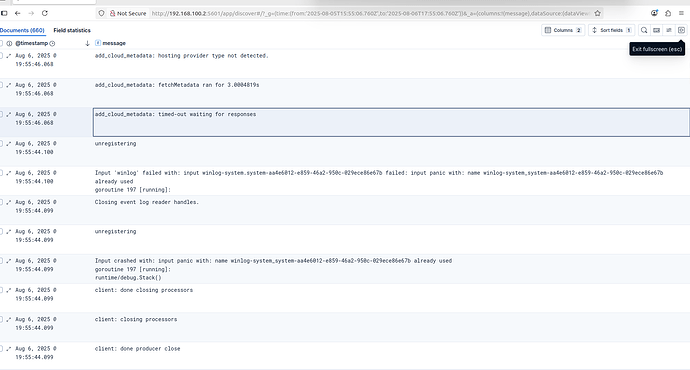
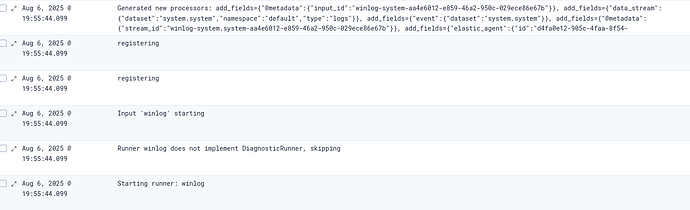
After a while I found out that I am getting a bunch of errors like this for every winlog configured
"message": "Input 'winlog' failed with: input winlog-windows.sysmon_operational-3de9734d-7e7a-418e-8255-c9b99eb35a87 failed: input panic with: name winlog-windows_sysmon_operational-3de9734d-7e7a-418e-8255-c9b99eb35a87 already used\ngoroutine 152 [running]:\nruntime/debug.Stack()\n\truntime/debug/stack.go:26 +0x5e\ngithub.com/elastic/beats/v7/filebeat/input/v2/input-cursor.(*managedInput).runSource.func1()\n\tgithub.com/elastic/beats/v7/filebeat/input/v2/input-cursor/input.go:172 +0x58\npanic({0x872a180?, 0xc0033074f0?})\n\truntime/panic.go:792 +0x132\ngithub.com/elastic/elastic-agent-libs/monitoring.panicErr(...)\n\tgithub.com/elastic/elastic-agent-libs@v0.20.0/monitoring/registry.go:287\ngithub.com/elastic/elastic-agent-libs/monitoring.(*Registry).Add(0xc00241f100, {0xc002171270?, 0xc00330e7e0?}, {0xa843860, 0xc00241fbc0}, 0x0?)\n\tgithub.com/elastic/elastic-agent-libs@v0.20.0/monitoring/registry.go:185 +0xca\ngithub.com/elastic/elastic-agent-libs/monitoring.(*Registry).NewRegistry(0xc00241f100, {0xc002171270, 0x46}, {0x0?, 0xa81af10?, 0x1?})\n\tgithub.com/elastic/elastic-agent-libs@v0.20.0/monitoring/registry.go:94 +0x155\ngithub.com/elastic/beats/v7/libbeat/monitoring/inputmon.NewInputRegistry({0x996d6aa, 0x6}, {0xc0025a5270, 0x46}, 0x0)\n\tgithub.com/elastic/beats/v7/libbeat/monitoring/inputmon/input.go:73 +0x36f\ngithub.com/elastic/beats/v7/winlogbeat/eventlog.newInputMetrics({0xc0025bed80, 0x24}, {0xc0025a5270?, 0xc001b6c050?})\n\tgithub.com/elastic/beats/v7/winlogbeat/eventlog/metrics.go:79 +0x56\ngithub.com/elastic/beats/v7/winlogbeat/eventlog.(*winEventLog).Open(0xc001ee8780, {{0x0, 0x0}, 0x0, {0x0, 0x0, 0x0}, {0x0, 0x0}})\n\tgithub.com/elastic/beats/v7/winlogbeat/eventlog/wineventlog.go:167 +0xda\ngithub.com/elastic/beats/v7/winlogbeat/eventlog.Run({0xa84f240, 0xc001ae0580}, {0xa8e6d88, 0xc001b6c050}, {0xa9056a0, 0xc001ee8780}, {{0x0, 0x0}, 0x0, {0x0, ...}, ...}, ...)\n\tgithub.com/elastic/beats/v7/winlogbeat/eventlog/runner.go:80 +0x331\ngithub.com/elastic/beats/v7/filebeat/input/winlog.winlogInput.Run({}, {0xc003132290, {0xc001de8240, 0x8e}, {0xc0025a5270, 0x46}, {0x996d6aa, 0x6}, {{0x99767c6, 0x8}, ...}, ...}, ...)\n\tgithub.com/elastic/beats/v7/filebeat/input/winlog/input.go:103 +0x3ff\ngithub.com/elastic/beats/v7/filebeat/input/v2/input-cursor.(*managedInput).runSource(_, {0xc003132290, {0xc001de8240, 0x8e}, {0xc0025a5270, 0x46}, {0x996d6aa, 0x6}, {{0x99767c6, 0x8}, ...}, ...}, ...)\n\tgithub.com/elastic/beats/v7/filebeat/input/v2/input-cursor/input.go:196 +0x483\ngithub.com/elastic/beats/v7/filebeat/input/v2/input-cursor.(*managedInput).Run.func1()\n\tgithub.com/elastic/beats/v7/filebeat/input/v2/input-cursor/input.go:151 +0x2f2\ngithub.com/elastic/go-concert/unison.(*MultiErrGroup).Go.func1()\n\tgithub.com/elastic/go-concert@v0.3.0/unison/multierrgroup.go:42 +0x66\ncreated by github.com/elastic/go-concert/unison.(*MultiErrGroup).Go in goroutine 259\n\tgithub.com/elastic/go-concert@v0.3.0/unison/multierrgroup.go:40 +0x76\n",
Even though the policy is quite simple and nothing dulicate in it. even when trying to delete all integrations inside the policy and creating a new "Windows" one => same issue.
- id: winlog-windows-3de9734d-7e7a-418e-8255-c9b99eb35a87
name: windows-1
revision: 1
type: winlog
use_output: default
meta:
package:
name: windows
version: 3.1.0
data_stream:
namespace: default
package_policy_id: 3de9734d-7e7a-418e-8255-c9b99eb35a87
streams:
- id: winlog-windows.powershell-3de9734d-7e7a-418e-8255-c9b99eb35a87
name: Windows PowerShell
data_stream:
dataset: windows.powershell
type: logs
condition: ${host.platform} == 'windows'
event_id: 400, 403, 600, 800
ignore_older: 72h
processors:
- translate_sid:
field: winlog.event_data.MemberSid
account_name_target: winlog.event_data._MemberUserName
domain_target: winlog.event_data._MemberDomain
account_type_target: winlog.event_data._MemberAccountType
ignore_missing: true
ignore_failure: true
- id: >-
winlog-windows.powershell_operational-3de9734d-7e7a-418e-8255-c9b99eb35a87
name: Microsoft-Windows-PowerShell/Operational
data_stream:
dataset: windows.powershell_operational
type: logs
condition: ${host.platform} == 'windows'
event_id: 4103, 4104, 4105, 4106
ignore_older: 72h
processors:
- translate_sid:
field: winlog.event_data.MemberSid
account_name_target: winlog.event_data._MemberUserName
domain_target: winlog.event_data._MemberDomain
account_type_target: winlog.event_data._MemberAccountType
ignore_missing: true
ignore_failure: true
- id: winlog-windows.sysmon_operational-3de9734d-7e7a-418e-8255-c9b99eb35a87
name: Microsoft-Windows-Sysmon/Operational
data_stream:
dataset: windows.sysmon_operational
type: logs
condition: ${host.platform} == 'windows'
ignore_older: 72h
processors:
- translate_sid:
field: winlog.event_data.MemberSid
account_name_target: winlog.event_data._MemberUserName
domain_target: winlog.event_data._MemberDomain
account_type_target: winlog.event_data._MemberAccountType
ignore_missing: true
ignore_failure: true
what could be causing this?