Hey people i am new to this forum, please help,
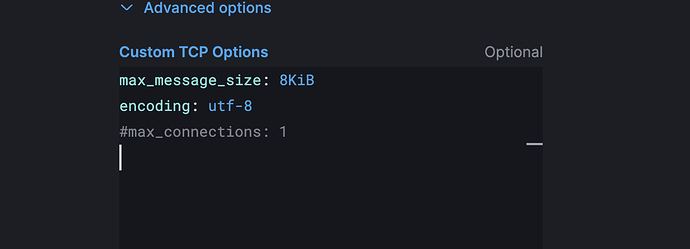
I have a problem with ESET integration, i connect it via TCP to collect JSON logs from it, my elastic/kibana is on-premis and ESET connect is a cloud one, so all is working but there an error you can see it on screen below
i have already wrote to ESET and they told me speak to Elastic