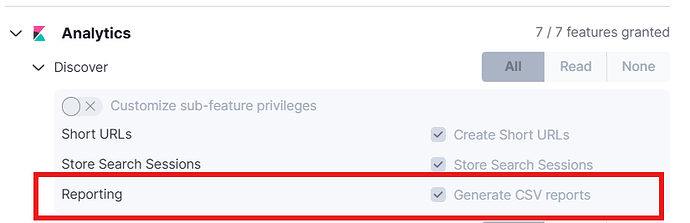
Hello,
I have an Elasticsearch+Kibana cluster set up (version 8.17.2). Regular users (given the editor) role cannot create CSV reports from Discover, while I (having the superuser role) can.
I have been trying to figure out which privileges I need to give a user to be able to generate reports. I am at a point where my custom role is identical to superuser:
GET /_security/role/superuser
{
"superuser": {
"cluster": [
"all"
],
"indices": [
{
"names": [
"*"
],
"privileges": [
"all"
],
"allow_restricted_indices": false
},
{
"names": [
"*"
],
"privileges": [
"monitor",
"read",
"view_index_metadata",
"read_cross_cluster"
],
"allow_restricted_indices": true
}
],
"applications": [
{
"application": "*",
"privileges": [
"*"
],
"resources": [
"*"
]
}
],
"run_as": [
"*"
],
"metadata": {
"_reserved": true
},
"transient_metadata": {},
"remote_indices": [
{
"names": [
"*"
],
"privileges": [
"all"
],
"allow_restricted_indices": false,
"clusters": [
"*"
]
},
{
"names": [
"*"
],
"privileges": [
"monitor",
"read",
"view_index_metadata",
"read_cross_cluster"
],
"allow_restricted_indices": true,
"clusters": [
"*"
]
}
],
"remote_cluster": [
{
"privileges": [
"monitor_enrich",
"monitor_stats"
],
"clusters": [
"*"
]
}
],
"description": "Grants full access to cluster management and data indices. This role also grants direct read-only access to restricted indices like .security. A user with this role can impersonate any other user in the system, manage security and create roles with unlimited privileges. Take extra care when assigning it to a user."
}
}
GET /_security/role/myrole
{
"myrole": {
"cluster": [
"all"
],
"indices": [
{
"names": [
"*"
],
"privileges": [
"all"
],
"allow_restricted_indices": false
},
{
"names": [
"*"
],
"privileges": [
"monitor",
"read",
"view_index_metadata",
"read_cross_cluster"
],
"allow_restricted_indices": true
}
],
"applications": [
{
"application": "*",
"privileges": [
"*"
],
"resources": [
"*"
]
}
],
"run_as": [
"*"
],
"metadata": {},
"transient_metadata": {
"enabled": true
},
"remote_indices": [
{
"names": [
"*"
],
"privileges": [
"all"
],
"allow_restricted_indices": false,
"clusters": [
"*"
]
},
{
"names": [
"*"
],
"privileges": [
"monitor",
"read",
"view_index_metadata",
"read_cross_cluster"
],
"allow_restricted_indices": true,
"clusters": [
"*"
]
}
],
"remote_cluster": [
{
"privileges": [
"monitor_enrich",
"monitor_stats"
],
"clusters": [
"*"
]
}
],
"description": "Grants full access to cluster management and data indices. This role also grants direct read-only access to restricted indices like .security. A user with this role can impersonate any other user in the system, manage security and create roles with unlimited privileges. Take extra care when assigning it to a user."
}
}
TLDR: Apart from metadata, the roles superuser and myrole are identical.
Despite this, if I assign the role myrole to a user, he won’t be able to generate reports (getting the error message Forbidden), but if I assign superuser, then CSV reports can be generated.
With privileges like this, the user is supposed to be able to generate reports, right?
Thanks in advance!
Regards,
Brumi